STORY AND PHOTOGRAPHY AUDREY ALLEN
INFOGRAPHIC EZRI COLPI
He smells the donuts before he even sees them. His six teammates gather around the box filled with cream sticks and glazed favorites, in preparation for the competition. East junior Aiden Ethier sits down at his computer in East Cyber Academy and computer science teacher Dave McKain’s room at nine a.m. on a Saturday. The team is currently competing in the “CyberPatriot”’ where they have to work together for six hours to fix a virtual machine. The timer counts down, and they anxiously wait to start. The buzzer sounds and Ethier quickly assesses what they need to do. This is the first round out of three but they came to end up on top.
The Lakota Cyber Academy was created in 2019 to provide students the resources and training necessary to fight cyber crime. It is the first of its kind and has been designed alongside 60 to 70 industry partners like Belcan, Kroger, and Procter & Gamble to develop a local pool of talent in the lucrative field of cyber security. With a wide range of industry-recognized cyber-focused courses, its curriculum is filled with highly valued certification opportunities and includes labs and a digital library.
“The industry that we have worked with the whole way through is Belcan. Belcan is an engineering firm in IT staffing and cybersecurity. They founded the Cyber Academy idea and tried to start it at another school and it didn’t really get off the ground,”Executive Director, Curriculum, and Instruction Keith Koehne told Spark. “They financially supported the program [at East] and have been a big supporter of it. We probably have an advisory board of about 20 people.”
East Director, Curriculum, and Instruction 7-12, Andrew Wheatley worked with some local colleges like Sinclar and University of Cincinnati to shape Cyber Academy.
“There are not many schools who are doing cybersecurity. There is not a state curriculum for cybersecurity. In fact, when we started this project, there was no national curriculum,” Wheatley told Spark. “We started to talk about what some college’s sequence of courses look like for cyber security and we had to make that work for a high school.”
Koehne said there are a million unfilled jobs in cybersecurity today, and there will be 3.5 million by the end of 2023 and if students are able to get their certifications through the program they can walk out of high school making $60,000 to $70,000 in their first year.
“It took the vision of somebody in our curriculum department looking at it saying, this is a growing and expanding field. We would make it very unique for us in Lakota to be able to offer to our students looking around not only the state, but the country,” East principal Rob Burnside told Spark. “This is not a program that most high schools are able to offer. We are blessed to have Mr. McKain here who has done a great job and is certainly well-respected in the industry.”
This is his McKain’s third year teaching Cyber Academy. He is a big advocate of cybersecurity and was thrilled to be able to help to build the curriculum. He works very closely with his students to establish a connection throughout their three years in the program.
“The story goes that four years ago, Matt Miller was talking with a friend of his, and they started talking about this idea of creating a cyber academy because cybersecurity is such a huge deal. It’s not going away,” McKain told Spark. “We don’t have enough people to fill all the jobs and they had this dream of creating this thing and managed to make things work pretty quickly.”

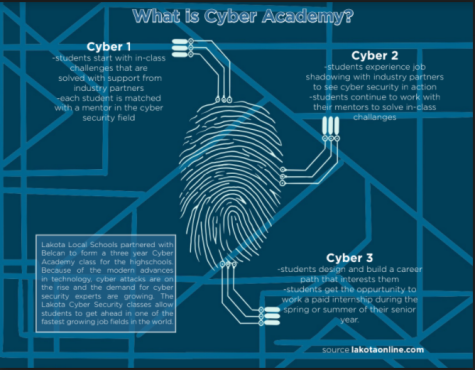
Classes
Cyber courses One, Two, and Three are designed to partner hands-on in-class challenges with online preparation for industry certifications in cyber security.
“The first year is a lot about system administration and understanding how things work,” McKain said. “They get under the surface a bit, because most people just live right on the surface and don’t really understand what’s going on beneath the surface with a lot of cybersecurity sprinkled in along with some competitions.”
East students valued the approach, including East junior and Cyber One student Adam Fagile.
“I’ve learned how to utilize a computer to do more tasks and how to increase personal security,” Faglie told Spark. “Being able to compete in the Cyberstart competition was my favorite thing because I was able to get a lot of exposure to what it’s like to work in cybersecurity.”
Cyber Two is a College Credit Plus (CCP) course through Sinclair University. The goal is to prepare students so that they can earn their security plus certification before they even graduate. They will experience job shadowing with industry partners to see the world of cybersecurity in action.
“The CCP course that we are taking through Sinclair is going to take all year and at the end of the year we are going to take the security plus certification test,” East junior and Cyber Two student George Kolks told Spark. “The security plus certification is something that not many people in the cybersecurity field have.”
Cyber Three will be culminating a “build your own challenge” experience through which students can define the path and certifications that most interest them. This all ends with a paid internship in either the spring or summer of the student’s senior year.
“All of the 24 kids who are in Cyber Three are promised to get paid internships when they come through the program,” Koehne said. “ We work with INTERalliance and they are able to provide six to 10 kids a year with an internship. We hope to grow our class to 50 to 70 kids in the next couple of years. So having that number of kids getting internships, we will probably have to start looking outside of this area.”
East senior and Cyber Three student Zoey Chappell received an internship at a company that she will go to a couple days after school.
“I did get an internship at Standex Electronics. I start on Nov. 8. One of the employees at Standex is a Lakota parent and heard about the program. He reached out to Mr. McKain to set it up,” Chappell told Spark. “I interviewed with them, and I’ll essentially be addressing cyber vulnerabilities found through an application Standex uses.”
Competitions
All three classes compete in many different types of competitions throughout the year including CyberPatriot, National Cyber League, and Cyberstart America.CyberPatriot is a group competition run by the AirForce and defense giant corporation Northrop Gruman. It is typically held in the fall and there are three different rounds.
“For the CyberPatriot competition we are given a virtual machine, and it is vulnerable in a lot of different ways. We have to change things to make it less vulnerable and make it more secure. As a team, we work for six hours straight from nine to three on a Saturday,” Ethier told Spark. “We finished the first round a couple of weeks ago, and in November we have our second round. The state round is in December. My group is 13th in Ohio for that competition as of now.”
 National Cyber League (NCL) competition happens once in the fall and once in the spring. It enables students to prepare and test themselves against practical cybersecurity challenges that they will likely face in the workforce, such as identifying hackers from forensic data, pentesting and auditing vulnerable websites, and recovering from ransomware attacks. Some of the puzzles are based on forensics, cryptography, web exploration, reverse engineering, and binary exploitation.
National Cyber League (NCL) competition happens once in the fall and once in the spring. It enables students to prepare and test themselves against practical cybersecurity challenges that they will likely face in the workforce, such as identifying hackers from forensic data, pentesting and auditing vulnerable websites, and recovering from ransomware attacks. Some of the puzzles are based on forensics, cryptography, web exploration, reverse engineering, and binary exploitation.
“One of the categories in the NCL is open source intelligence, which is just, they give you something you have to look up and find a flag. One example would be, they give you an image and you have to figure out when the image was taken, where it was taken, and what camera was used. Or something could be encoded and you’d have to decode it,” Ethier said. “Just this past NCL I got to the gold bracket, which is in the top 15% in America, which is especially cool since most of them are college age and older.”
Cyberstart America,created in 2020, starts in October and runs all the way through April. It is available to students all year so they can go in and tackle problems when they have time. There is scholarship money attached to this competition that makes it an exciting opportunity for students.
“I did well enough in Cyberstart America to qualify as a finalist. I was given a free certification course, and I did that over the summer which would have been $30,000,” Ethier said. “I got it for free and I now have a certification in the cybersecurity world.”
Mentorships
In Cyber One, each student in the Academy will be matched with a mentor in the field that they meet once a month to serve as a resource and help guide students through the program and beyond.
“We have a strategic partnership coordinator, Katie Bauer, who makes connections with all of our industry partners. It is really word of mouth,” Koehne said. “I think it is one of those things where one person gets involved and then they go back and tell their friends. They enjoy working with the kids and are excited to bring people in.”
The mentors give them advice, talk to them about what they do, and guide them throughout the Cyber Academy course.
“Having a mentor is really cool because you get to talk to people who are in the cyber field. My mentor right now is Justin Hall and he works for Cincinnati Bell,” Ethier said. “It’s super cool to hear about the issues he runs into.”
According to the U.S. Bureau of Labor Statistics, about 16,300 openings for information security analysts on average have been projected each year over the past decade. Many of those openings are expected to result from the need to replace workers who transfer to different occupations or exit the labor force, such as to retire.
“The first thing [McKain] told us when we got into the room was that if we finished this plan all throughout high school, we could probably not go to college and get a job that paid 30K a year. Apparently there’s 30% of jobs that need to be filled,” Kolks said. “Companies love that we’re doing this and the companies will come to our school and they’ll pay for our competition tickets. P&G last year paid for some of our tickets.”
Issues
Due to restrictions on the school-issued Chromebooks, students are having a hard time trying to work on competitions and programs.
“I wish we had more machines and programs and being able to work more on the Chromebooks would really help us in competitions,” Kolks said. “We’ve had so many competitions reach out to us because we’re such a big program saying that they would sponsor us, but it’s just so hard to get across with all the blocked stuff on the Chromebooks. I understand, but it is a little frustrating.”
Everyday the students use their Chromebooks to do their work for the class and have specific programs and tools that they need to use and open to complete their assignments.
“We use the computers a ton, but especially for Cyberstart America. As I’m going through these challenges I’m like ‘I can’t do that’ because I can’t access the inspect tool’. The whole point of the inspect tool is it is only on your browser at that moment,” said Ethier. “There is probably a good reason why Lakota has it restricted but it’d just be great if we could use that tool.”
Impact
Despite the disadvantages, there are many reasons why people should enter this program and take the classes even if they do not know anything about the cyber field.
“Mr. McKain is really good at walking you through everything. I started out having no computer knowledge. I wanted to do something with computers but not coding. You have no need for entrance level knowledge and basically all of Cyber One is basics,” Ethier said. “You learn so much so quickly so don’t worry about not knowing enough going in. Just apply yourself and take the time to learn the commands.”
These students not only learn about cybersecurity and how to hack into things, but they learn important life lessons that are becoming more prominent in society as technology advances.
“Everything that we touch in our hands that is electronic, can be hacked at any time. [This class] really taught me to be careful with my stuff,” Kolks said. “Before Cyber One, I had my social security number in my notes on my phone, but when I started this course I took it immediately off. I just learned to be more careful with my passwords and to be smarter online.”